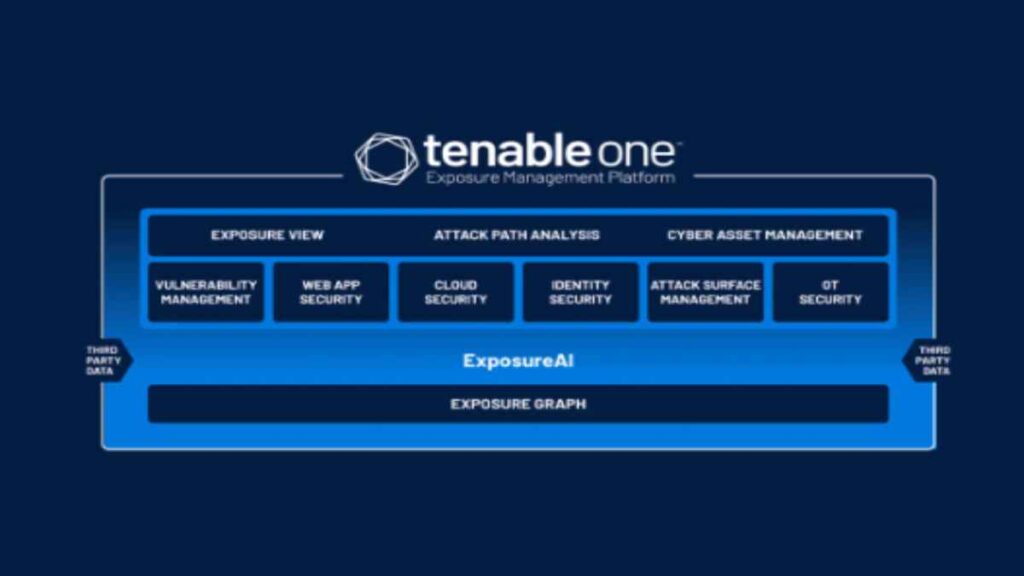
The modern digital landscape is evolving rapidly, and with it, the need for robust security frameworks. As cyber threats grow more sophisticated, organizations must ensure that their systems remain secure while maintaining operational efficiency. One of the core components of this security framework is Tenable Identity Exposure Architecture.
This architecture plays a pivotal role in managing and mitigating risks associated with identity vulnerabilities. With businesses increasingly relying on digital systems and cloud-based technologies, safeguarding sensitive identity data is critical to preventing security breaches.
In this article, we’ll delve into how Tenable’s Identity Exposure Architecture enhances both security and risk management. We’ll explore its functionality, benefits, challenges, and best practices for implementation. Additionally, we will review some common customer experiences with the system and discuss its potential side effects.
What Is Tenable Identity Exposure Architecture?
Tenable Identity Exposure Architecture refers to a comprehensive framework designed to identify, manage, and mitigate identity-related risks across an organization’s entire network. This architecture is central to ensuring that security policies effectively cover all aspects of identity exposure, including unauthorized access, data leaks, and potential cyber-attacks targeting vulnerable identities.
Unlike traditional identity management systems, Tenable’s architecture focuses on detecting exposure points within an organization’s identity infrastructure. It then works to safeguard against those vulnerabilities by applying a combination of monitoring, auditing, and proactive threat detection techniques.
This solution aligns with a growing trend in cybersecurity: to shift from merely defending against external threats to proactively monitoring and managing internal vulnerabilities, such as exposed identities, that may serve as entry points for cybercriminals.
Why Tenable Identity Exposure Architecture Is Essential for Security and Risk Management
As businesses transition to more complex IT environments, the surface area for potential threats grows. Identity exposure often emerges as one of the most significant risk factors in modern cybersecurity.
Key Security Concerns Addressed by Tenable:
- Unauthorized access to critical systems
- Exposure of personal or corporate data due to weak identity management practices
- Insufficient visibility into the entire identity lifecycle
By implementing Tenable Identity Exposure Architecture, organizations can gain deeper visibility into identity-related risks, enabling faster response times and more comprehensive threat management. Through continuous monitoring and advanced analysis, it detects potential breaches or identity exposures before they can escalate.
Benefits of Tenable Identity Exposure Architecture
1. Enhanced Visibility and Control
Tenable Identity Exposure Architecture provides organizations with real-time insights into their identity infrastructure, helping to monitor and manage vulnerabilities continuously. This proactive monitoring allows businesses to identify weak spots and patch them promptly before they become security liabilities.
2. Streamlined Risk Mitigation
Risk management is greatly improved with the architecture’s ability to highlight threats associated with compromised identities. By automating the detection process, it simplifies the identification of high-risk exposure points that require immediate attention.
3. Comprehensive Security Compliance
The architecture also supports compliance with industry standards, ensuring that organizations meet regulatory requirements related to identity protection, such as GDPR, HIPAA, and other data privacy regulations. By securing exposed identities, businesses reduce the risk of non-compliance penalties.
4. Faster Response Times
A key benefit of Tenable Identity Exposure Architecture is its speed in detecting and responding to incidents. This capability minimizes the time cybercriminals have to exploit vulnerabilities, reducing the chances of a successful attack.
How Tenable Identity Exposure Architecture Works
Tenable’s Identity Exposure Architecture works through a series of integrated components designed to identify vulnerabilities in an organization’s identity management system. The architecture is based on the following processes:
- Discovery and Assessment: The system first discovers all active identities within the network, assessing their security posture by identifying any vulnerabilities or gaps.
- Continuous Monitoring: Once the identities are assessed, continuous monitoring is implemented to detect unusual behavior, potential exposure, or unauthorized access attempts.
- Incident Response: When an anomaly is detected, Tenable Identity Exposure Architecture triggers automated alerts and assists in the response process by isolating affected systems and initiating remediation steps.
- Reporting and Analysis: The system provides detailed reports on identity exposure risks and security posture, offering recommendations for improvement.
By continuously monitoring these processes, the architecture allows organizations to maintain a strong security posture while minimizing manual intervention.
Key Features of Tenable Identity Exposure Architecture
- Comprehensive Identity Discovery: Automatically identifies all identities, both human and non-human, across the entire network.
- Real-time Risk Assessment: Provides up-to-date risk assessments, allowing organizations to address vulnerabilities proactively.
- Advanced Threat Detection: Detects threats through AI-powered anomaly detection algorithms.
- Automated Compliance Reports: Generates reports to ensure ongoing compliance with regulatory requirements.
These features allow organizations to scale their identity security efforts efficiently and effectively.
Customer Reviews and Experiences with Tenable Identity Exposure Architecture
Customer Reviews:
-
“Tenable’s Identity Exposure Architecture has greatly improved our ability to manage identity risks. The automated monitoring and alerts have given us peace of mind knowing that we can quickly detect vulnerabilities.” – IT Security Manager at Global Enterprises Inc.
-
“The real-time visibility into our identity exposure has been a game changer. We’ve seen a significant reduction in the number of unauthorized access attempts since implementing the system.” – CISO at Financial Corporation
Customer Experiences:
- Many customers have praised the ease of integration with their existing infrastructure, including their identity management and access control systems.
- Some users have mentioned that the reporting features are detailed and user-friendly, enabling their security teams to take immediate action when needed.
Side Effects and Potential Challenges
While Tenable Identity Exposure Architecture offers robust security features, organizations must consider potential side effects:
- System Overload: Continuous monitoring and data collection may lead to system performance issues if not properly configured.
- False Positives: Although rare, the system may occasionally flag legitimate activity as suspicious, requiring manual validation.
However, these issues can be mitigated with proper configuration and tuning during the initial setup phase.
Conclusion: Why Tenable Identity Exposure Architecture Matters
The modern security landscape demands that organizations proactively manage and mitigate risks, especially those related to identity exposure. Tenable Identity Exposure Architecture provides an essential layer of defense by detecting and responding to identity-related threats before they can compromise sensitive systems.
By offering enhanced visibility, streamlined risk management, and compliance features, Tenable ensures that organizations can confidently address potential vulnerabilities in their identity management systems. With the added benefits of faster response times and real-time threat detection, Tenable Identity Exposure Architecture proves to be an invaluable tool for modern cybersecurity.
FAQ:
-
What is Tenable Identity Exposure Architecture? Tenable Identity Exposure Architecture is a security framework designed to manage and mitigate risks associated with exposed identities in a network, offering real-time monitoring and proactive threat detection.
-
How does Tenable’s architecture help with risk management? By identifying vulnerabilities related to identity exposure, Tenable’s architecture enhances risk management by automating detection, monitoring, and response processes.
-
Can Tenable’s architecture integrate with existing security systems? Yes, Tenable’s architecture integrates seamlessly with other identity management and security solutions, providing enhanced protection without disrupting existing workflows.
-
What are the key benefits of Tenable Identity Exposure Architecture? Key benefits include enhanced visibility into identity-related risks, compliance with industry standards, streamlined risk mitigation, and faster incident response times.
-
Are there any side effects of using Tenable Identity Exposure Architecture? Potential side effects include system performance issues if not properly configured and the occasional occurrence of false positives. Proper setup and tuning can minimize these effects.